
Source: https://xkcd.com/1782/
Table of Contents
1. Introduction
To mobilize a growing number of activists an open-source, self-hosted team communication & collaboration platform could be used, which is implemented in the InspIRCd software (Internet Relay Chat technology, IRC).
IRC technology has ultra-low requirements on bandwidth and is recommended in world regions where IT hardware has low performance or internet connection is weak or expensive, thereby, replacing modern, high-requirements platforms like MATTERMOST.
In addition, IRC scales well to highly complex communication networks, also because of a (simple) command-line interface. For example, the modern Libera.Chat IRC network features 22,503 channels on different topics (as of 2022-06-16).
Furthermore, open technologies (e.g. Email, Mastodon, IRC) cannot be owned and controlled by corporations (e.g. Meta/Facebook, Twitter, Google) to act against public interests. Thereby, IRC technology supports people power and freedom of speech.
The additional complexity of IRC and related technologies is caused by the open technological standards (e.g. IRC protocol), which allows users to implement custom-made, modular solutions and the surrounding hacking culture, which supports innovation and a competition of ideas.
Although IRC technology may cause an additional burden for users. e.g. entering simple text commands in chat buffer, this technological burden is expected to be worth the effort, since IRC is consistent with the objectives of progressive movements. In addition, IRC technology can be on various levels of complexity deepening on user experience and preference.
Therefore, my expectation is that IRC technology can contribute tactically and strategically to the objectives of progressive civil resistance movements.
In the following, I describe how to install an Internet Relay Chat server, which is available at https://web.dhub.chat as a browser-based web app or via irc://irc.dhub.chat:6697 via an IRC client using a TLS-secured communication channel.
2. Overview
The following hardware and software stack will be used:
2.1 Hardware (HOSTING.DE)
- Infrastructure as a Service (IaaS) provider: http://hosting.de
- “Cloud Server SmallServer”
- CPU: 1 core
- Memory: 1 GB
- Storage: 20 GB
- Costs: 5,15 EUR/Month
2.2 Software
The software stack (server-side) includes the following software components (in logical order of installation):
- Operating System: Debian 12
- Firewall: Uncomplicated Firewall (UFW) (https://code.launchpad.net/ufw)
- Web server: Nginx (“engine x”, https://nginx.org)
Note: This is HTTP and reverse proxy server for handling internet requests from clients using web browsers. - Certificate authority: Let’s encrypt (https://letsencrypt.org)
Note: A free, automated, and open certificate authority to certify that the web address is directed to expected IP address and secure, encrypted communication between client and server is used. - IRC server: InspIRCd (https://www.inspircd.org)
Note: InspIRCd is advertised as stable, modern and lightweight, high-performance, open-source, free IRC server. - IRC services: Anope (https://www.anope.org)
Note: Anope implements various services clients to maintain an IRC network, e.g. NickServ as nickname management service and ChanServ as channel management service. - IRC proxy (IRC Bouncer): Quassel (https://quassel-irc.org)
Note: Quassel is a modern IRC client-server(core) software. The Quassel Server (core) servers as a proxy server mainting a permanent connection to the IRC server, which collects all communication in a client has joined, allowing flexibility for the client to attach and detach without missing out on communication. - IRC Bot: Eggdrop (https://www.eggheads.org)
Note: An IRC bot allows the control of a IRC network, e.g. by sending messages to channels or banning users. - Mail server: Postfix (http://www.postfix.org)
- Web app: The Lounge (https://thelounge.chat)
Note: A web-based IRC client for self-hosting.
2.3 Important features
-
- User Interfaces:
- Web-based user interface, e.g. web.dhub.chat
- Desktop-based user interface, e.g. Quassel IRC client
- Command-line user interface, e.g. weechat IRC client
- User Interfaces:
- Privacy:
- Anonymity:
- temporary, arbitrary user names (“nicks, “nicknames”), ie no permanent user account and password required
- hiding of IP addresses (“cloaking”)
- Encryption (optional: IRC can be used for public broadcasting vs. private messaging!)
- TSL-encrypted connection between client and server (Watch out: The server admin has access to all information on the server, however, will keep to strict confidentiality.)
- Encrypted connections for private messages between clients (peer-to-peer) are available (cf Blowfish, Off-The-Record, depending on IRC client)
- Integrity:
- The software architecture is maintained to ensure the integrity of the system, however, services will be provided by IT professionals non-profit which limits the available resources and response times!
- Anonymity:
- Optional IRC Services (in progress):
- Nick services: Management of user names (“nicks”), channels, and administrators (“opers”), e.g. ANOPE (https://www.anope.org)
- Bouncer services: Permanent storage of IRC conversations, e.g. QUASSEL (client/server, https://quassel-irc.org)
3. Install Operating System (DEBIAN)
The cloud service provider hosting.de offers pre-installed cloud servers, where Debian 12 (“Bookworm”) can be selected as operating system. During the purchase of the cloud server a password is requested for the superuser “root” account.
After the installation of the bare-bone OS the following steps should be performed:
Local, user> ssh root@<ipaddress> Remote, root> apt update Remote, root> apt upgrade Remote, root> apt-get install sudo Remote, root> apt-get install emacs # optional: alternatively use pre-installed editors "nano" or "pico" Remote, root> dpgk-reconfigure locales # en_US-UTF-8 is preferred to easily share error reports in English in social networks for faster support Remote, root> adduser irchat # add standard user with superuser privileges, to be able to deactivate root account later for security reasonsRemote, root> sudo usermod -aG sudo irchat # add irchat to superuser group Remote, irchat> su irchat # switch to irchat user
4. Install Firewall (UFW)
Install UFW (Uncomplicated FireWall):
Remote, irchat> sudo apt install ufw
Remote, irchat> sudo ufw allow ssh # important otherwise you lose ssh connection and have to connect via hosting.de website via VNC.
Remote, irchat> sudo ufw allow 6667/tcp # unencrypted IRC connection
Remote, irchat> sudo ufw allow 6667/udp # unencrypted IRC connection
Remote, irchat> sudo ufw allow 6697/udp # TSL-encrypted IRC connection
Remote, irchat> sudo ufw allow 6697/tcp # TSL-encrypted IRC connection
Remote, irchat> sudo ufw allow 80/tcp # unencrypted http connection
Remote, irchat> sudo ufw allow 80/udp # unencrypted http connection
Remote, irchat> sudo ufw allow 443/udp # TSL-encrypted https connection
Remote, irchat> sudo ufw allow 443/tcp # TSL-encrypted https connection
Remote, irchat> sudo ufw allow 4242/udp # optional: for QuasselCore
Remote, irchat> sudo ufw allow 4242/tcp # optional: for QuasselCore
Remote, irchat> sudo ufw enable
Remote, irchat> sudo ufw status5. Configure Domain services (NAMECHEAP.COM)
The corresponding domains were registered and configured at the service provide namecheap.com:
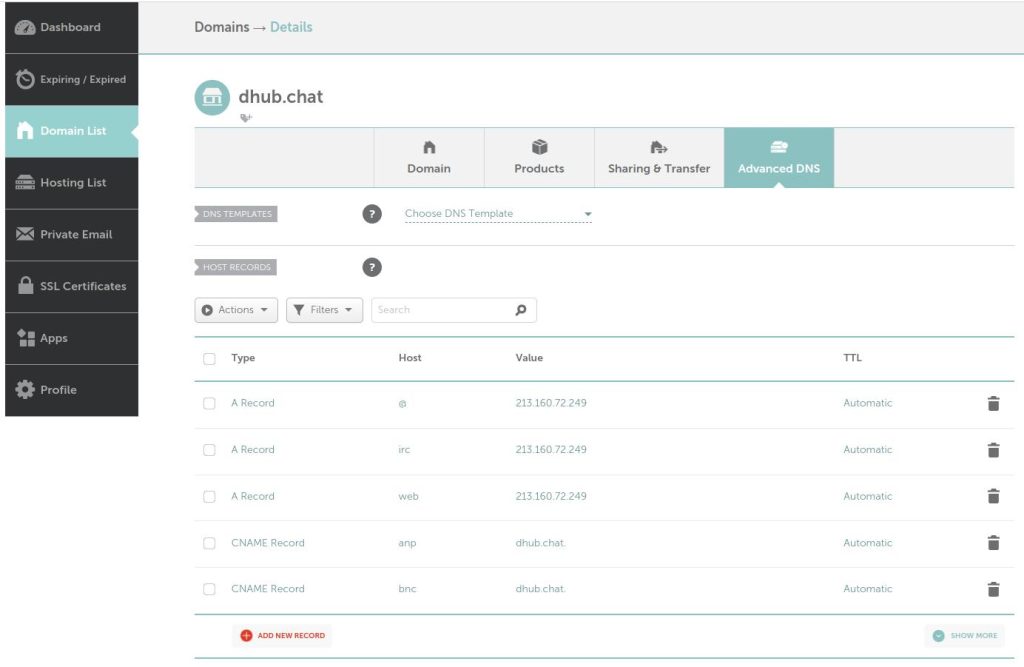
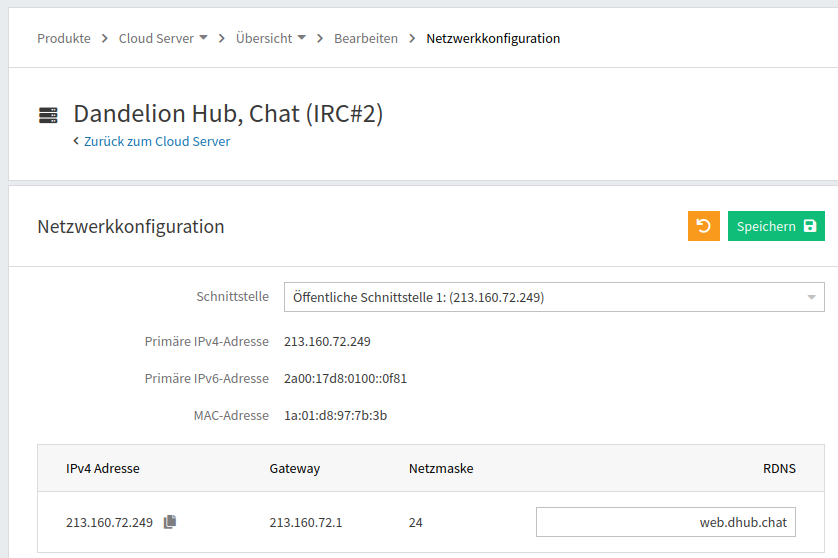
In addition, at the cloud service provided the reverse DNS (RDNS) entry needs to be set to the web address of the web app:
6. Install Web Server and Certificates (NGINX, CERTBOT)
Instructions on how to install the NGINX software can be found elsewhere [REF].
Remote, irchat> sudo apt install nginx certbot python3-certbot-nginx
Remote, irchat> sudo certbot --nginx --cert-name dhub.chat-d irc.dhub.chat,web.dhub.chat,www.dhub.chat,dhub.chat
Remote, irchat> # Note: If you forgot a subdomain, you can add it by repeating all domains AND the additional domain:
Remote, irchat> sudo certbot certificates # check existing certificates
Remote, irchat> sudo certbot --nginx --cert-name dhub.chat --expand -d irc.dhub.chat,web.dhub.chat,www.dhub.chat,dhub.chat,additional.dhub.chatInstructions on how to configure the NGINX software can be found elsewhere [REF].
Remote, irchat> cp /etc/nginx/sites-available/default /etc/nginx/sites-available/default.backup # backup default NGINX configuration file to be able to restore if something goes wrong
Remote, irchat> emacs /etc/nginx/sites-available/default # alternatively, use pico or nano as editors# /etc/nginx/sites-available/default
...
server {
root /var/www/html;
index index.html index.htm index.nginx-debian.html;
server_name dhub.chat www.dhub.chat web.dhub.chat; # managed by Certbot
location / {
proxy_pass http://127.0.0.1:9000/;
proxy_http_version 1.1;
proxy_set_header Connection "upgrade";
proxy_set_header Upgrade $http_upgrade;
proxy_set_header X-Forwarded-For $remote_addr;
proxy_set_header X-Forwarded-Proto $scheme;
#by default nginx times our connections in one minute
proxy_read_timeout 1d;
}
listen [::]:443 ssl ipv6only=on; # managed by Certbot
listen 443 ssl; # managed by Certbot
ssl_certificate /etc/letsencrypt/live/dhub.chat/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/dhub.chat/privkey.pem; # managed by Certbot
include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot
}The configuration of the NGINX software can be tested and the server reloaded or completely restarted to make the changes active:
Remote, irchat> sudo nginx -t # test configuration before making active
Remote, irchat> sudo systemctl status nginx # show whether change of configs was successful and server is running
Remote, irchat> sudo systemctl reload nginx # reload configuration into web server without interrupting services
Remote, irchat> sudo systemctl restart nginx # reload configuration into web server without interrupting servicesThe InspIRCd software and TheLounge software require TSL certificates to be able to provide secure communication with the associated web addresses, ie this is irc.dhub.chat for InspIRCd and web.dhub.chat for TheLounge. To avoid read access problems (e.g. caused by AppArmor on Linux), it is recommended to copy the original certificate files into the configuration folder of InspIRCd:
Remote, irchat> cp -Lr /etc/letsencrypt/live/dhub.chat/ /etc/inspircd/certificates/7. Install IRC server (INSPIRCD)
Instructions on how to install the InspIRCd software can be found elsewhere [1-4].
Note: Use apt-get install not apt install, which may show a minor bug.
Remote, irchat> mkdir ~/inspircd_install/Remote, irchat> cd ~/inspircd_install/
Remote, irchat> wget https://github.com/inspircd/inspircd/releases/download/v3.16.1/inspircd_3.16.1.deb12u1_amd64.deb
Remote, irchat> sudo apt-get install ./inspircd_3.16.1.deb12u1_amd64.deb
Instructions on how to configure the InspIRCd software can be found elsewhere [1, 5]. The configuration of the IRC server is complex. It is recommended to copy the main configuration example files from /usr/share/doc/inspircd/ to /etc/inspircd/.
It is recommended to go through the main example config files inspircd.conf and modules.conf and read the documentation in the config files to get a better understanding of its functionality, and compare the default configs with the configs of the updated configuration files [6,7,8].
Remote, irchat> cat /etc/inspircd/help.txt
Remote, irchat> ls -la /usr/share/doc/inspircd/
Remote, irchat> # inspircd.conf
Remote, irchat> cp /usr/share/doc/inspircd/inspircd.conf.example.gz /etc/inspircd/inspircd.conf.example.gz
Remote, irchat> gunzip /etc/inspircd/inspircd.conf.example.gz
Remote, irchat> mv /etc/inspircd/inspircd.conf.example /etc/inspircd/inspircd.conf
Remote, irchat> # modules.conf
Remote, irchat> cp /usr/share/doc/inspircd/modules.conf.example.gz /etc/inspircd/modules.conf.example.gz
Remote, irchat> gunzip /etc/inspircd/modules.conf.example.gz
Remote, irchat> mv /etc/inspircd/modules.conf.example /etc/inspircd/modules.conf
Remote, irchat> # motd.txt
Remote, irchat> cp /usr/share/doc/inspircd/motd.txt.example /etc/inspircd/motd.txt
Remote, irchat> chown irc:irc /run/inspircd/ # allow irc to save process identifier to directoryAfter InspIRCd was installed and preliminarily configured, the IRC server can be started with one of the following commands:
Remote, irchat> # Recommended for Production
Remote, irchat> sudo systemctl start inspircd.service
Remote, irchat> sudo systemctl status inspircd.service
Remote, irchat> sudo systemctl restart inspircd.service # useful for a clean restart of the IRC server after change in configs without interruption of service
Remote, irchat> sudo systemctl reload inspircd.service # useful for an update of the IRC server after change in configs without interruption of service
Remote, irchat> sudo journalctl -xe # show logs and errors
Remote, irchat> # Recommended for Development (Debugging)
Remote, irchat> sudo -g irc -u irc /usr/bin/inspircd --debug --nofork # outputs log and error stream to console
Remote, irchat> ps -aux | grep inspircd # find process id
Remote, irchat> kill -9 <pid>
Remote, irchat> sudo -g irc -u irc /usr/bin/inspircd # restart with updated configs as background process without output of logs and errors in console7.1 TLS-encrypted connections
# inspircd.conf
#-#-#-#-#-#-#-#-#-#-#-#- PORT CONFIGURATION -#-#-#-#-#-#-#-#-#-#-#-
<bind
address="*"
port="6697"
type="clients"
sslprofile="Clients"
defer="0"
free="no">
...<sslprofile name="Clients"
provider="gnutls"
cafile=""
certfile="/etc/inspircd/certificates/dhub.chat/fullchain.pem"
crlfile=""
dhfile=""
hash="sha256"
keyfile="/etc/inspircd/certificates/dhub.chat/privkey.pem"
mindhbits="1024"
outrecsize="2048"
priority="NORMAL"
requestclientcert="yes"
strictpriority="no">
...
Server certificates (.pem files) are valid for 90 days and are then auto-renewed by certification bot (certbot tool), however, only in the /etc/letsencrypt/live/ folder. However, the copies of the certificates for the IRC service (inspircd) are located in the /etc/inspircd/certificates folder. Therefore, the certificates should be copied automatically in regulator intervals to avoid a disruption of services because of invalid certificates. The following cronjob copies the certificates, changes owner and group and restart the inspircd service, so the new certificates are applied.
- Create the following script at /home/irchat/inspircd_run/irc_update_certs.sh
#!/bin/sh
rsync --copy-links /etc/letsencrypt/live/dhub.chat/* /etc/inspircd/certificates/dhub.chat/
chown -R irc:irc /etc/inspircd/certificates/dhub.chat/
systemctl restart inspircd.service- Create a cronjob which is run as superuser (to be able to access the certificates) every sunday:
- $>select-editor # choose your preferred editor
- $>sudo cronjob -e
- Add line “* * * * 0 /home/irchat/inspircd_run/irc_update_certs.sh” and end line with linebreak (press enter)
7.2 Hiding of IP addresses (“cloaking”)
The configuration of hiding IP addresses of connecting clients (“cloaking”) requires activation of multiple modules, definition of a <cloak> tag, and the generation of an at least 30-character encryption key (use password generator at [13] ):
# modules.conf
...
<module name="cloaking">
...
<module name="conn_umodes">
...
<module name="md5">
...
<cloak mode="full"
key="<IamA30CharacterKey>"
prefix="dhub-"
ignorecase="no">
...
<module name="conn_join">
<autojoin channel="#dhub-meetngreet">
...
7.3 Set ADMIN and OPER credentials
The administrator credentials and operator (“Oper”) credentials need to be defined to be able to manage users and channels. For this purpose, passwords need to be defined in the config files (inspircd.conf, oper.conf). Although passwords can be defined as plaintext it is recommended to encrypt the passwords. The recommended encryption algorithm is “bcrypt”. The plaintext passwords can be encrypted in the inspircd server window (do not used the channel chat!) with the following command:
ircclient, ircserverlogwindow>/MKPASSWD bcrypt MySecretPassword123The encrypted (“hashed”) password will be display to the user in the IRC server log window of the user’s IRC client. Alternatively, you can also generate the encrypted password string with https://bcrypt.online.
The following lines need to be activated (uncommented) or updated, e.g. <connect> tags, in inspircd.conf:
<include file="/etc/inspircd/opers.conf">
...
<connect
hash="bcrypt"
password="$2a$10$<encryptedpasswordstring>"
...> Update the modules.conf file:
...
<module name="password_hash">
...
<module name="bcrypt">
...Update the opers.conf file:
<oper
name="dandelionhub"
hash="bcrypt"
password="$2a$10$<encryptedpasswordstring>"
host="*"
type="NetAdmin">8. Install IRC services (ANOPE)
Install Anope:
remote, irchat> sudo apt-get -y install anope
remote, irchat> sudo systemctl start anope.serviceConfigure /etc/inspircd/inspircd.conf :
...
<include file="/etc/inspircd/services/anope.conf">
# Code block from /etc/anope/services.conf, which goes int inspircd.conf!
<module name="hidechans">
<module name="services_account">
<module name="spanningtree">
<bind address="127.0.0.1" port="7000" type="servers">
<link name="anp.dhub.chat"
ipaddr="127.0.0.1"
port="7000"
sendpass="mypassword123"
recvpass="mypassword123">
<uline server="anp.dhub.chat" silent="yes">
...Configure /etc/anope/services.conf :
# see multiple changes in updated services.confNote:
- SSL to connect to the IRCd is not needed is you are connecting via localhost (ie ssl=no).
- You have to use a unique server hostname for Anope services, e.g. anp.dhub.chat (ie irc.dhub.chat already used by inspircd IRC server).
- Check that port numbers are identical in /etc/anope/services.conf and /etc/inspircd/inspircd.conf.
9. Install Mail server (Postfix)
Install Postfix mail server (so Anope can send emails to user, e.g. to reset password) [22]:
remote, irchat> sudo apt install postfix mutt remote, irchat> sudo ufw allow Postfix # Tell your cloud provider to open port 25 too! remote, irchat> sudo ufw allow 25/tcp # Tell your cloud provider to open port 25 too! remote, irchat> sudo ufw allow 25/udp # Tell your cloud provider to open port 25 too! remote, irchat> sudo dpkg-reconfigure postfix # General mail configuration type: Internet Site # System mail name (ie email domain): dhub.chat # Recipient for root and postmaster mail (ie use existing username): irchat # Other destinations to accept mail for: dhub.chat, dhub.chat, localhost.chat, , localhost # Force synchronous updates on mail queue: No # Local networks: 127.0.0.0/8 [::ffff:127.0.0.0]/104 [::1]/128 # Use procmail for local delivery: Yes # Mailbox size limit: 0 # Local address extension character: + # Internet protocols to use: Allremote, irchat> sudo emacs /etc/postfix/main.cf # Optional: If you have to update the configuration, or just re-run 'sudo dpkg-reconfigure postfix'remote, irchat> sudo systemctl reload postfix
Note: Ask your cloud provider (here: hosting.de) to open port 25 (SMTP). Many disable it by default to block mass spammers.
Test the Postfix installation:
remote, irchat> telnet localhost 25 remote, irchat> telnet localhost 25 # with terminal output, Enter STRG+] and quit to leave telnet terminal
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
220 dhub.chat ESMTP Postfix (Debian/GNU)
remote, irchat> sudo mutt -s "Test from your new mailserver" your.name@provider.com < /dev/null # send test email # will be sent from root@dhub.chat
Note:
- This is a minimal SMTP email server to send emails. The mailserver cannot receive emails with this configuration. Sent emails may be filtered to spam by mail providers because email authentication records are not set.
- To use the email domain as a fully functional email server, I recommend to use a professional email provider with a custom domain (see tutorial for protonmail [23]). To ensure that emails are not blocked or filtered to spam the email authentication (SPF/DKIM/DMARC) records need to be set correctly.
- With this configuration, the sent emails are not encrypted. Therefore, it is not recommmended to ask ANOPE to send your password to your email, but just a temporary code to reset your password. You can then reset your password with the temporary code in a IRC client with a secure TSL-connection. To configure Postfix with TSL-certificates enabling encryption [24].
- Emails from IRC services (Anope) will be sent from <no-reply@dhub.chat> (cf /etc/anope/services.conf, “sendfrom” parameter).
10. Install IRC Proxy (QUASSEL)
Note (2023-12-23): The QUASSEL project offering a modern IRC client and bouncer does not seem to be maintained since January 2022. While the basic functionality still works, it is not the recommended solution. Therefore, the alternatives are connecting to IRC from a server, which stays connected to the IRC network, or to use irccloud.com, which offers an IRC client and a bouncer (and other commercial services).
Install QuasselCore as IRC Proxy (IRC Bouncer) with default SQLite database [14-21]:
Remote, irchat> sudo apt-get install quassel-core
Remote, irchat> sudo systemctl status quasselcore # check where config files are stored: /var/lib/quassel/
Remote, irchat> sudo mv /var/lib/quassel/quasselCert.pem /var/lib/quassel/quasselCert.pem.backup
Remote, irchat> sudo cat /etc/letsencrypt/live/dhub.chat/{fullchain,privkey}.pem >> /var/lib/quassel/quasselCert.pem
Remote, irchat> sudo systemctl restart quasselcore
Remote, irchat>sudo quasselcore --configdir=/var/lib/quassel --add-user dandelionhub
Remote, irchat> sudo ufw allow 4242/tcp
Remote, irchat> sudo ufw allow 4242/udpMigrate to PostGres Database for performance and functionality:
Remote, irchat> sudo apt-get -y install postgresql libqt5sql5-psql
Remote, irchat> sudo -u postgres psql
Remote, postgres> CREATE USER quassel ENCRYPTED PASSWORD 'somepassword123';
Remote, postgres> CREATE DATABASE quassel WITH OWNER quassel ENCODING 'UTF8';
Remote, postgres> \quit
Remote, irchat> sudo quasselcore --configdir=/var/lib/quassel --select-backend=PostgreSQL
Remote, irchat> sudo quasselcore --configdir=/var/lib/quassel --add-user dandelionhub # create user also in postgres database with default password
Remote, irchat>sudo quasselcore --configdir=/var/lib/quassel --change-userpass dandelionhub # set user password
Remote, irchat> sudo quasselcore --configdir=/var/lib/quassel & # systemctl doesnot work after switching to postgres databaseExamine PostGres Database, e.g. check registered users (you can also connect via database client, e..g dbeaver via port 5432 after opening firewall):
Remote, irchat> sudo -u postgres psql
Remote, postgres> \l # list databases
Remote, postgres> \c quassel # connect to quassel database (default databases are postgres, template0, template1)
Remote, postgres> \dt # list tables
Remote, postgres> select username from quasseluser;
Remote, postgres> \qServer certificates (.pem files) are valid for 90 days and are then auto-renewed by certification bot (openssl tool). The following cronjob creates the certificates, changes owner and group and restart the QUASSEL service, so the new certificates are applied.
- Create the following script at /home/irchat/quassel_run/quassel_update_certs.sh
#!/bin/sh # sudo openssl req -x509 -nodes -days 365 -newkey rsa:4096 -keyout /var/lib/quassel/quasselCert.pem -out /var/lib/quassel/quasselCert.pem -batch # self-certified cat /etc/letsencrypt/live/dhub.chat/{fullchain,privkey}.pem >> /var/lib/quassel/quasselCert.pem # certified by let's encryptchown quasselcore:quassel /var/lib/quassel/quasselCert.pem killall quasselcore sudo quasselcore --configdir=/var/lib/quassel &
- Create a cronjob which is run as superuser (to be able to access the certificates) at the 1st day of each month:
- $>select-editor # choose your preferred editor
- $>sudo cronjob -e
- Add line “0 0 1 * * /home/irchat/quassel_run/quassel_update_certs.sh” and end line with linebreak (press enter)
11. Install web app (TheLounge)
Instructions on how to install the IRC web app TheLounge software can be found elsewhere [9-11].
Remote, irchat> mkdir ~/thelounge_install/
Remote, irchat> cd ~/thelounge_install/
Remote, irchat> wget https://github.com/thelounge/thelounge-deb/releases/download/v4.4.1/thelounge_4.4.1_all.deb
Remote, irchat> sudo apt-get install ./thelounge_4.4.1_all.deb
Instructions on how to configure the IRC web app TheLounge software can be found elsewhere [12].
Remote, irchat> mkdir /home/irchat/thelounge_run/certificates
Remote, irchat> sudo systemctl start thelounge.service
12. Install IRC Bot (Eggdrop)
Install Eggdrop (IRC Bot) [25-27]:
Remote, irchat> sudo apt install tcl tk tcl-dev tk-devRemote, irchat> mkdir -p /home/irchat/eggdrop_install/
Remote, irchat> sudo ufw allow 5555/tcp
Remote, irchat> sudo ufw allow 5555/udp
Remote, irchat> cd /home/irchat/eggdrop_install/
Remote, irchat> wget https://ftp.eggheads.org/pub/eggdrop/source/1.9/eggdrop-1.9.5.tar.gz
Remote, irchat> tar -xzvf /eggdrop-1.9.5.tar.gz ./eggdrop-1.9.5/
Remote, irchat> cd ./eggdrop-1.9.5/
Remote, irchat> ./configure
Remote, irchat> make config
Remote, irchat> make
Remote, irchat> make install
Remote, irchat> make sslcert DEST=/home/irchat/eggdrop_run/
Remote, irchat> cd /home/irchat/eggdrop_run/
# !!! Read and edit your config file eggdrop-basic.conf (for new users) or eggdrop.conf (for advanced users) completely!!!
# !!! set owner "<nameofowner>" (eg the IRC network admin name), DO NOT set owner "<nameofbot>"!
# Path to executable binary file: /home/irchat/eggdrop_run/eggdrop
Remote, irchat> ./eggdrop -m eggdrop-basic.conf # First run
Remote, irchat> chmod u+x eggdrop-basic.conf #2nd+ runs
Remote, irchat> ./eggdrop-basic.conf # #2nd+ runs, run script as executable
Remote, irchat> ./scripts/autobotchk eggdrop-basic.conf # create CRON job (to autostart bot)
Control eggdrop via “The Party Line” channel:
Via /dcc chat: Go to IRC chat window and login as admin, which you have defined in the inspircd.conf file above, let’s with nick “dandelionhub”. Note: To connect to the partyline via /dcc your IRC client needs to support the direct-client-to-client (dcc) command, e.g. weechat, IceChat, XChat, mIRC, but not QUASSEL, TheLounge, or IRCcloud (client-core based IRC clients). Switch to dcc-enabled client before executing the following commands:
Remote, irc message window> /oper dandelionhub ThisIsTheAdminPassword # register as admin
Remote, irc message window> /msg dhub_guard hello # contact eggdrop by its nick "dhub_guard" and say hello, this makes you the owner of the bot
Remote, irc message window> /msg dhub_guard pass ThisIsTheBotAdminPassword # define the admin password for the bot
Remote, irc message window> /dcc chat dhub_guard # works only in clients supporting dcc, e.g. weechat, IceChat, XChat, mIRC, but not QUASSEL, TheLounge, or IRCcloudVia telnet:
Note: You need to configure a non-ssl, plain text port in the eggdrop-basic.conf file, but you do not have to open the port in the firewall, if you are already on the host where eggdrop is installed.
Remote, irchat> telnet 0.0.0.0 6666 # via plain-text port, enter NEW or the nickname of the user which has already said "hello" to the bot
Remote, irchat> openssl s_client -cert my.crt -key my.key -connect 0.0.0.0:5555 # via SSL-secured port (not tested)
# 1) Enter nickname of owner of eggdropb, ie the name of the owner as defined in the eggdrop-basic.conf while ("cf set owner <owner>" command)
# 2) Enter Password of ownerCommands for “The Partyline”:
Some examples of using “The Partyline” (via telnet):
Remote, Eggdrop, Partyline> .help # show overview of commands
Remote, Eggdrop, Partyline>.help whois # get documenation for specific command <whois>
Remote, Eggdrop, Partyline>.rehash # reload eggdrop-basic.conf after changes to configuration
Remote, Eggdrop, Partyline>.tcl # check whether TCL script is enabled
Remote, Eggdrop, Partyline>.tcl source /home/irchat/eggdrop_run/scripts/dccwhois.tcl # read TCL script, eg https://docs.eggheads.org/tutorials/firstscript.html
# Note: If you copy and paste text scripts to your console from a website, the character coding system may need to be adjusted, eg from ISO-Latin 8859-1 to ISO-UTF-8 (or whatever your server is using):Tracing errors in the config of the IRC bot:
Remote, irchat> ./eggdrop -mnt eggdrop-basic.conf # First run
Remote, eggdrop> .console +d
Remote, irchat> openssl s_client -connect irc.dhub.chat:6697 -CApath /etc/ssl/certs/ # check SSL certificates see also:
- Writing an Eggdrop Script [29]
- How to Write an Eggdrop Module [30]
- Eggdrop Tcl Archive [31]
Note: To have be always connected to the partyline via the terminal/telnet, even if you disconnect from server, you can run a terminal multiplexer like tmux [28] in the background so you can disconnect and later reconnect to the server via ssh and the tmux session ($>tmux attach).
References
[1] https://ubuntu.com/tutorials/irc-server (outdated)
[2] https://docs.inspircd.org/3/installation/debian/
[3] https://github.com/inspircd/inspircd/releases/tag/v3.16.1
[4] https://github.com/inspircd/inspircd/releases/download/v3.16.1/inspircd_3.16.1.deb12u1_amd64.deb
[5] https://docs.inspircd.org/3/configuration/
[6] dhub.chat inspircd.conf (main configs)
[7] dhub.chat modules.conf (configs of modules)
[8] dhub.chat motd.conf (Message Of The Day, ie Welcome Message)
[9] https://thelounge.chat/docs/install-and-upgrade#debian-and-ubuntu-based-distributions
[10] https://github.com/thelounge/thelounge-deb/releases/latest
[11] https://github.com/thelounge/thelounge-deb/releases/download/v4.4.1/thelounge_4.4.1_all.deb
[12] https://thelounge.chat/docs/configuration
[13] https://nordpass.com/password-generator/
[14] https://bugs.quassel-irc.org/projects/quassel-irc/wiki
[15] https://orcacore.com/install-postgresql-debian-12-bookworm/
[16] https://quassel-irc.org/faq/cert
[17] https://troubles.noblogs.org/post/2018/04/24/quassel-and-lets-encrypt/
[18] https://bugs.quassel-irc.org/projects/quassel-irc/wiki/PostgreSQL
[19] https://bugs.quassel-irc.org/issues/1526?next_issue_id=1525&prev_issue_id=1527
[20] https://bugs.quassel-irc.org/projects/quassel-irc/wiki/Manage_core_users
[21] https://bugs.quassel-irc.org/projects/quassel-irc/wiki/Blowfish_Encryption_Manual
[22] https://ubuntu.com/server/docs/mail-postfix
[23] https://proton.me/support/custom-domain
[24] https://upcloud.com/resources/tutorials/secure-postfix-using-lets-encrypt
[25] https://docs.eggheads.org/tutorials/firststeps.html
[26] https://www.linuxpackage.com/debian/install-tcl%20tk-on-debian
[27] https://docs.eggheads.org/install/install.html
[28] https://www.hamvocke.com/blog/a-quick-and-easy-guide-to-tmux/
[29] Writing an Eggdrop Script, https://docs.eggheads.org/tutorials/firstscript.html
[30]How to Write an Eggdrop Module, https://docs.eggheads.org/modules/writing.html
[31] http://tclarchive.org/
TODO:
- Run all services as standard user
- Install TSL certificate to Postfix
- Install CRON job to copy updated TSL certificates to InspIRCd, Anope, Quasselcore, Postfix, (NGINX automatic)